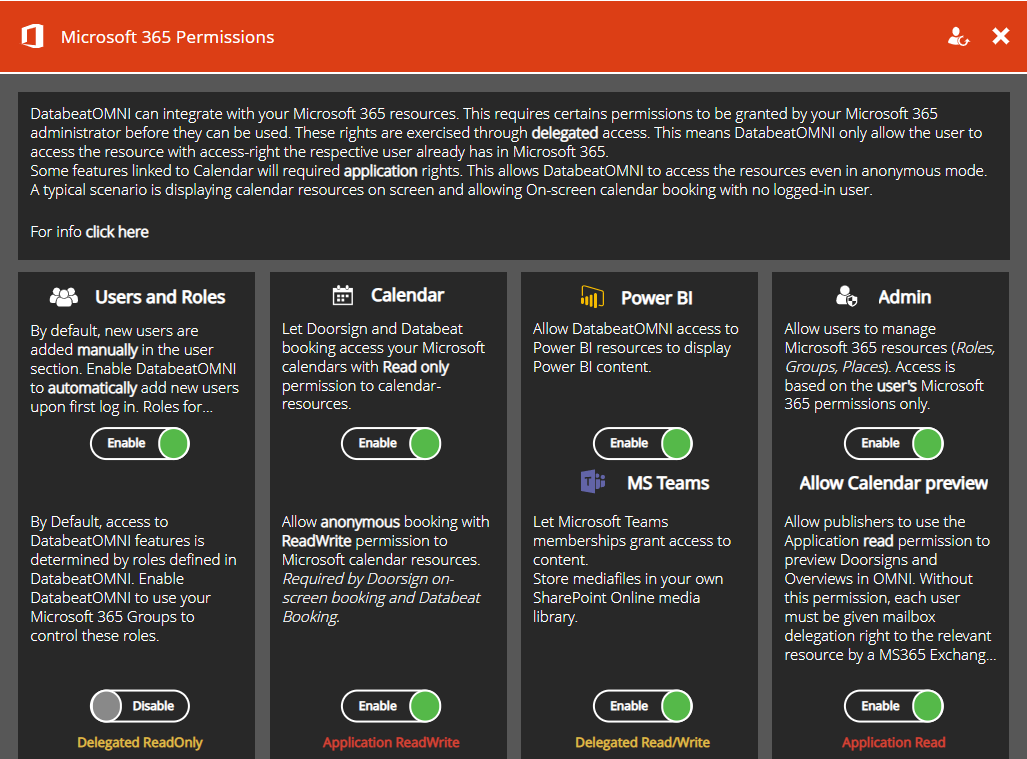
How to enable DatabeatOMNI authentication and integration with Microsoft 365. What technologies and methods are used and what permissions do we have to provide to DatabeatOMNI.
There are two levels of Integration
- Authentication Allow users to log in to DatabeatOMNI with their Microsoft 365 credentials. It is simpler, more secure and aligned with your organisation's user and authentication regime.
We strongly recommend all Microsoft 365 customers to use Microsoft 365 authentication.
It is simpler to manage, simpler to use, more secure and more flexible.
- Integration Based on Microsoft 365 authentication, integrations allow users to access, publish and share Microsoft 365 content in DatabeatOMNI. Currently, Calendar and Microsoft Power BI integrations are implemented. More integrations and features are planned.
Access to Microsoft 365 - Microsoft Graph
DatabeatOMNI access Microsoft Office through Microsoft Graph. "The Gateway to data and intelligence in Microsoft Office 365" It is a set of API's that allow DatabeatOMNI to securely access, read and write Microsoft 365 resources. Using Microsoft's own APIs ensures that we follow Microsoft's guidelines and best practices.
Other solutions do integrations through PowerShell access and scripting, which is considered less secure and poses a higher security risk.
DatabeatOMNI has been tested, verified and certified by Microsoft. It can be found and access through the Microsoft Azure marketplace.
More Info (from Microsoft):
Microsoft Graph Permission Reference
Authentication and Authorization basics for Microsoft Graph
Setting up the DatabeatOMNI Office 365 Integration
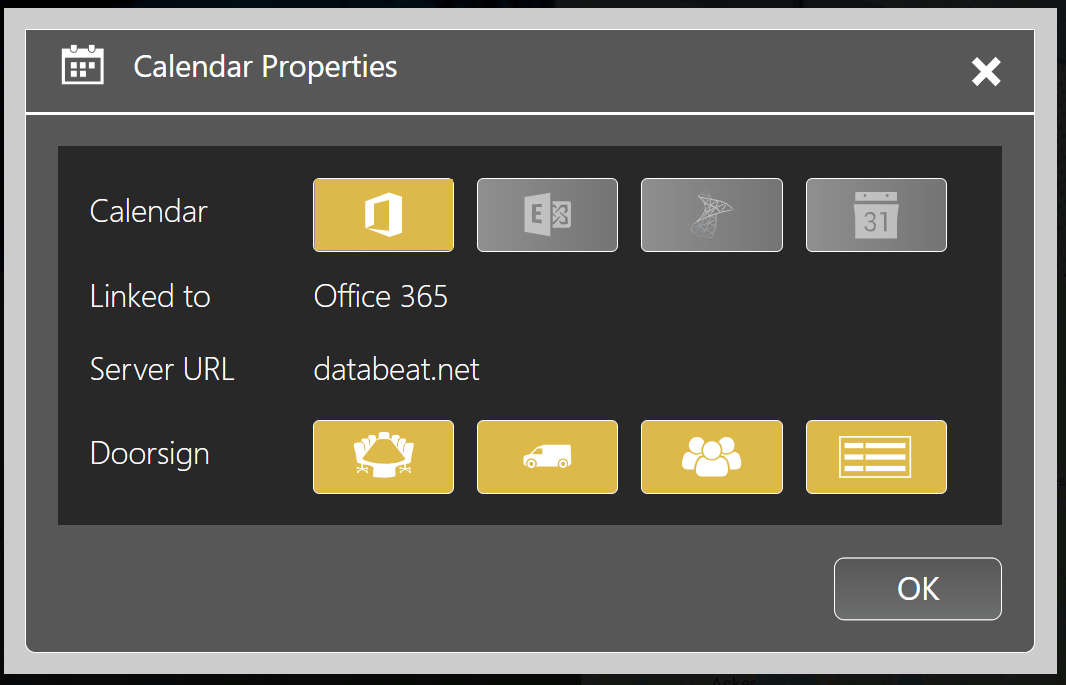
There are two kinds of Integrations :
Delegated Permission are used by DatabeatOMNI with a signed-in user present. DatabeatOMNI acts on behalf of the signed-in user to access MS-Graph.
Delegated permissions are used by DatabeatOMNI when in the Databeat administrative and publishing tool. We believe that any permission should be based on the organisation's policy and limited to the signed-in users rights.
Application Permission are used by DatabeatOMNI without a signed-in user present. This is ONLY applicable when there is no signed-in user present. This is relevant for DatabeatOMNI doorsign and way-finding solutions that shows info from calendars and in some instances (when booking are to be made on-screen). In these instances there are no signed-in user (it is only the screen with no logged-in user).
Microsoft's: "Permission Requested Accept for your organisation"
When request is being made, you will receive this information from Microsoft. It provided detailed information about the permission that has been requested by DatabeatOMNI. This depends on which settings and integrations you want to do.
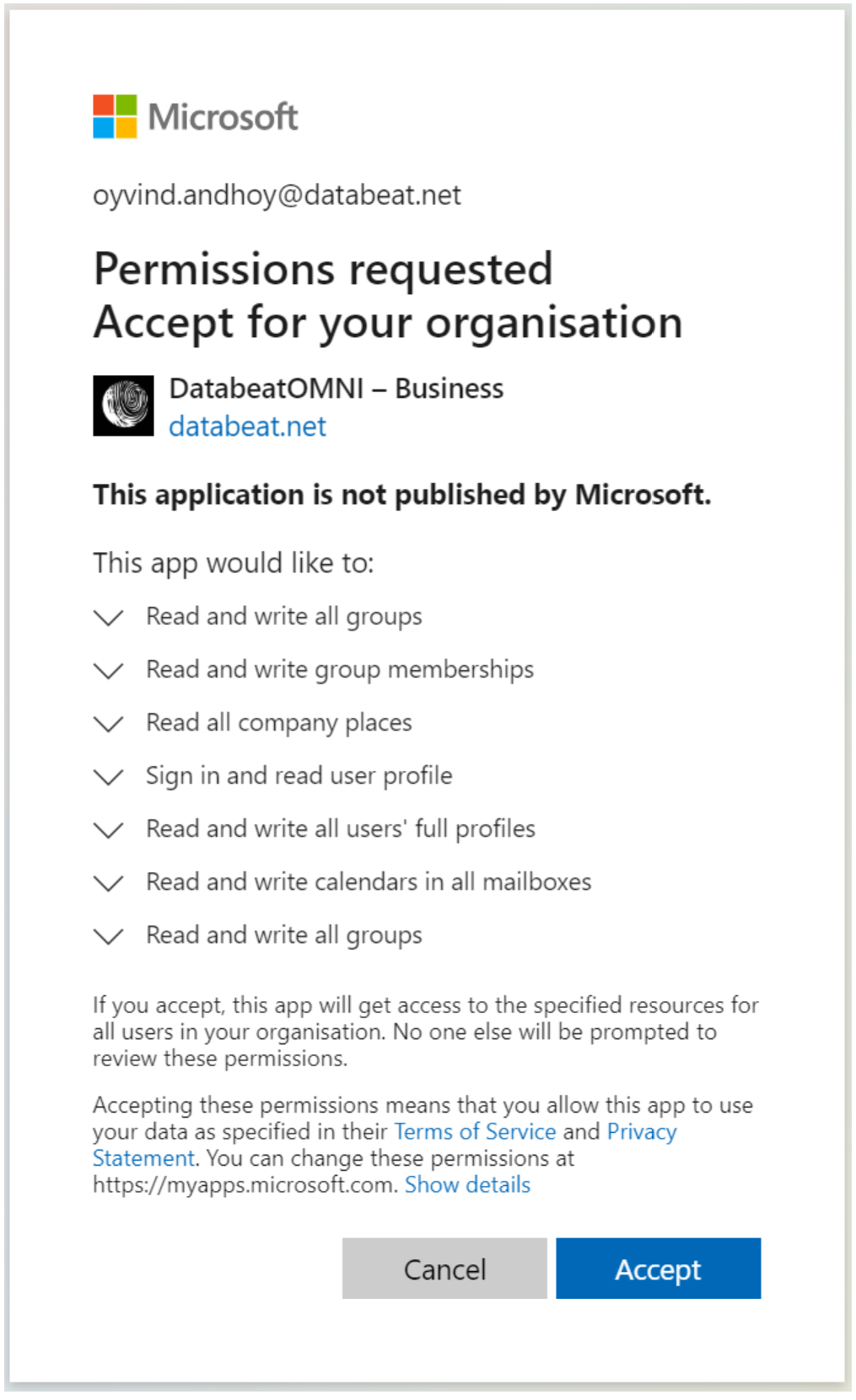
Notice that each request has a pull-down icon to allow you to see more, for example
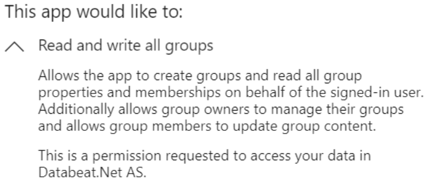
Notice the wording ... on behalf of the signed-in user. This describes a delegated permission.
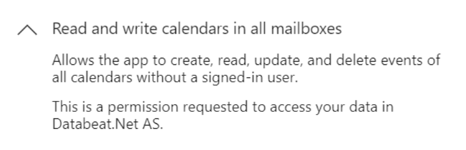
Notice the wording ...without a signed-in user. This describes an application permission.
Access to Microsoft PowerBI
DatabeatOMNI links to the Office 365 universe with MS Graph API and will integrate with Microsoft Power BI even without Application permission and Calendar access.
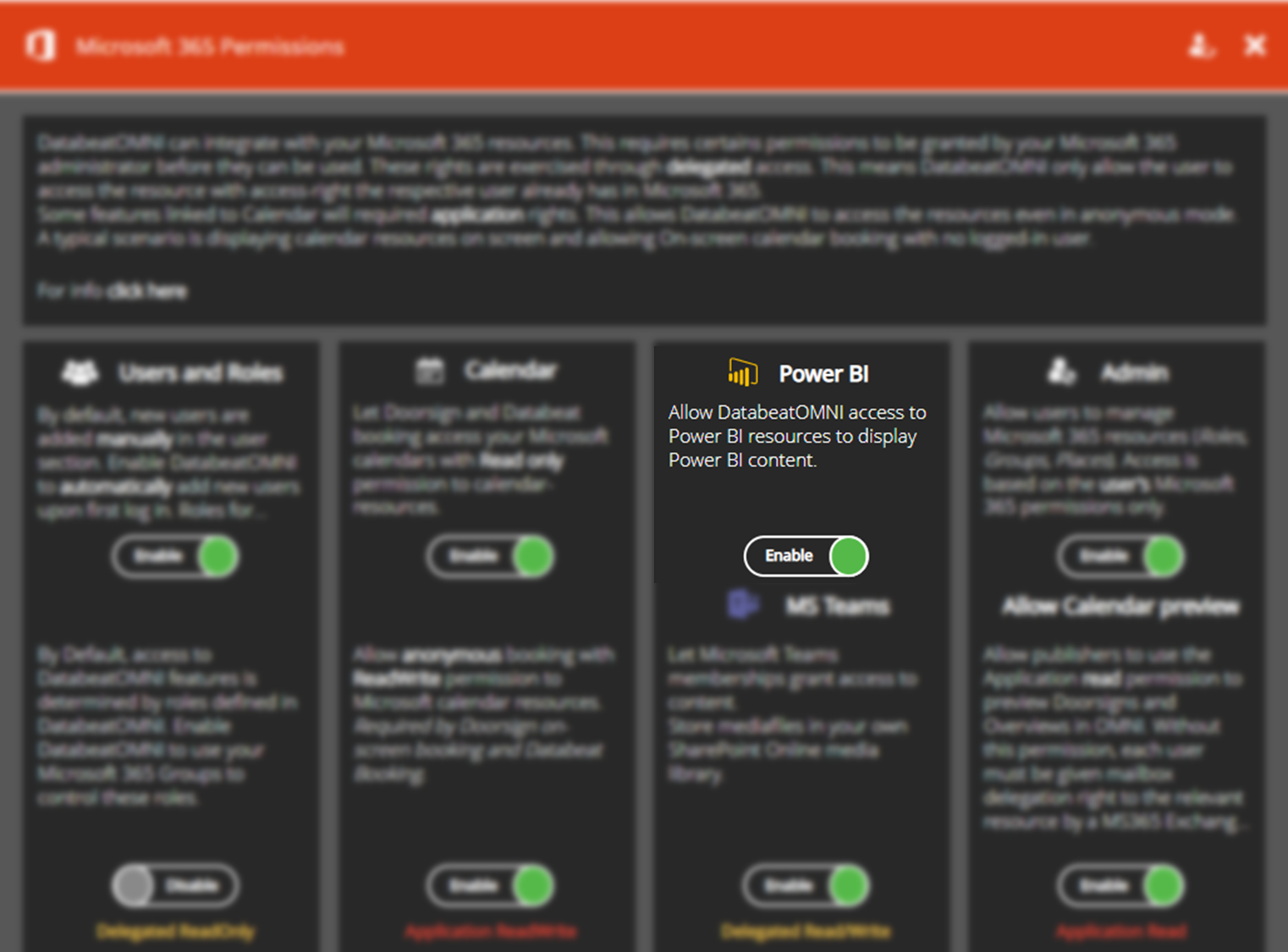
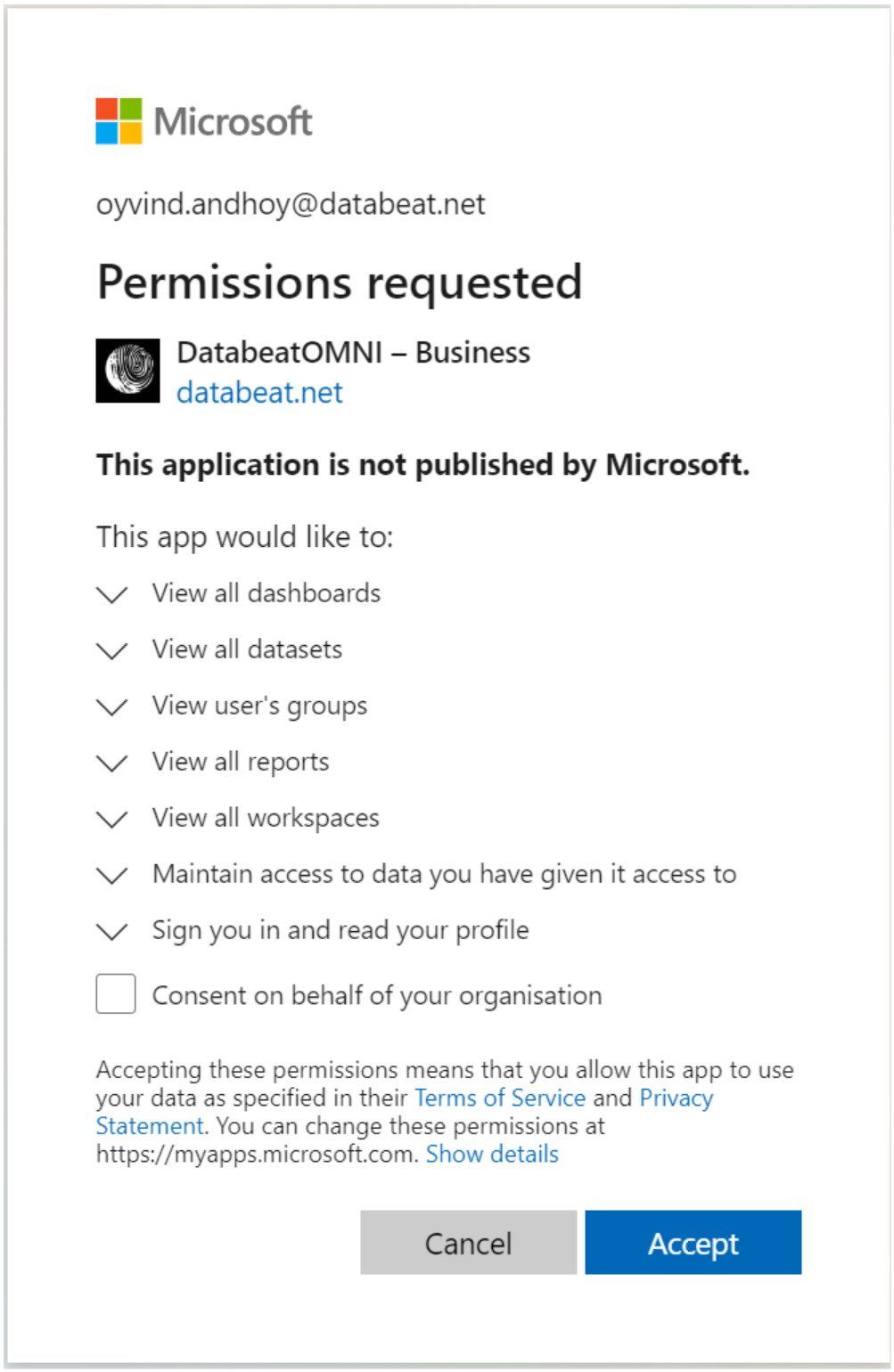
When you first time access Power BI in the OMNIboard or Screendesigner widget you will be presented and grant permissions to the following :
Is it secure ?
Anyone working with security would agree that nothing is 100% secure. Security is about risk and risk is factor of probability and consequence. We in Databeat have taken every step we believe is possible to make this as secure as possible. Microsoft is a company whose reputation on security directly impacts considerable revenue, and they take it very seriously, therefore we trust Microsoft. By using Office 365 applications and user management, so do you.
By using Microsoft technologies for authentication and access, best practices and submitting it to Microsoft for certification, we believe we have taken every step possible to make it as secure as possible.
Should you have any questions and input to this, we will be happy to hear from you.